Computer viruses spread through various channels, making it essential to understand their transmission methods. They can infect systems via email attachments, malicious downloads, or compromised websites. Once introduced to a system, a computer virus can quickly replicate and spread to other connected devices, posing a significant threat to your digital security.
Common pathways for computer virus transmission include removable media, such as USB drives and CDs, which can carry and transfer viruses between devices. Additionally, computer viruses can spread through network connections, especially if network security is weak. By being aware of these pathways, you can take preventive measures to protect your devices from infection.
To prevent the spread of computer viruses, adopt comprehensive security practices. Regularly update your software and operating system to close security gaps. Avoid downloading files from untrusted sources and be cautious when opening email attachments. Implementing strong security measures helps contain and prevent the spread of computer viruses, safeguarding your digital environment.
Table of Contents
1. Email Attachments
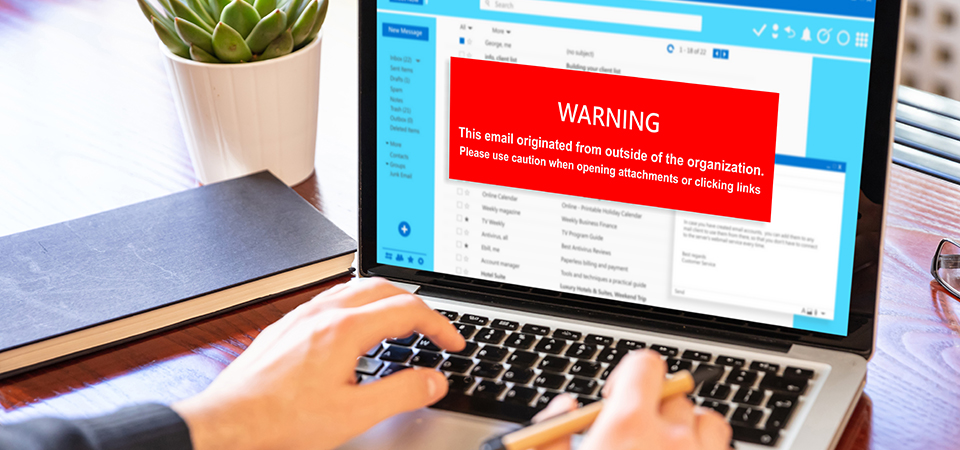
Email attachments are a common vector for spreading computer viruses. These malicious files can be disguised as harmless documents, images, or other types of files, making it easy for unsuspecting users to open them. Once opened, the computer virus can quickly infect the user’s system, potentially spreading to other computers within the network.
To protect against computer viruses, it’s crucial to be cautious when handling email attachments, especially from unknown or untrusted sources. Always scan attachments with antivirus software before opening them. Even seemingly legitimate emails can be compromised, so it’s essential to verify the sender’s identity if something looks suspicious.
In addition to using antivirus software, educating users about the risks of email attachments can significantly reduce the spread of computer viruses. Encourage safe email practices, such as not downloading unexpected attachments and being wary of links within emails. By staying vigilant, users can help prevent the proliferation of computer viruses through email attachments.
Common Tactics Used
Common tactics used in email attachments to spread a computer virus include disguising malicious files as legitimate documents. Cybercriminals often send these attachments with names that look like invoices, reports, or other routine files, tricking recipients into opening them. Once opened, the computer virus can install itself and start spreading to other systems.
Another tactic is to use compressed files, such as ZIP or RAR archives, to hide the computer virus. These compressed files can bypass certain security measures, making it easier for the virus to reach its target. Users might be less suspicious of a compressed file, especially if it appears to come from a trusted source, increasing the likelihood of the virus being unleashed.
Phishing emails are also a prevalent method for delivering a computer virus via email attachments. These emails often appear to come from reputable organizations and urge recipients to open the attached file immediately. By creating a sense of urgency or fear, cybercriminals can prompt users to bypass their usual caution, leading to the spread of the computer virus.
How to Recognize Suspicious Emails
Recognizing suspicious emails is crucial in preventing a computer virus from infiltrating your system. One key indicator is an unknown sender or an email address that looks slightly altered from a familiar one. Cybercriminals often mimic trusted contacts to make their emails seem legitimate, so always double-check the sender’s address for any inconsistencies.
Another sign of a potentially malicious email is urgent or alarming language, urging immediate action. Emails that pressure you to open attachments or click on links without proper context should raise a red flag. This tactic aims to bypass your usual cautious behavior, increasing the risk of downloading a computer virus.
Be wary of unexpected attachments or links, especially if the email content seems generic or impersonal. Legitimate emails from trusted sources usually provide context or explanations for attachments. If you receive an unsolicited attachment or a link with minimal explanation, it’s best to verify with the sender directly before interacting with the email to avoid a computer virus infection.
2. Malicious Downloads

Malicious downloads are a primary method by which a computer virus can infect your system. These downloads often come from untrustworthy websites or through deceptive pop-up ads that trick users into clicking on them. Once downloaded, the computer virus can compromise your data, steal sensitive information, or disrupt your system’s operations.
To avoid falling victim to malicious downloads, it’s essential to download software and files only from reputable sources. Always verify the legitimacy of the website and ensure it uses secure protocols, such as HTTPS. Cybercriminals often create convincing replicas of trusted sites to distribute a computer virus, so vigilance is necessary.
Using robust antivirus software can also help protect against malicious downloads. Antivirus programs can detect and block harmful files before they cause any damage. Regularly updating your antivirus software ensures it can recognize and neutralize the latest computer virus threats, providing an additional layer of security for your system.
Risks of Unverified Software
Downloading unverified software poses significant risks, as it often serves as a conduit for a computer virus. Cybercriminals embed malicious code within seemingly legitimate programs, which then infect your system upon installation. This computer virus can steal sensitive data, cause system malfunctions, or open backdoors for further attacks.
One major risk of unverified software is the potential for widespread system damage. Once a computer virus is introduced, it can spread rapidly, corrupting files and disrupting normal operations. This not only impacts personal users but can also compromise entire networks, leading to costly repairs and data recovery efforts.
To mitigate these risks, it’s crucial to verify the source of any software before downloading. Stick to reputable platforms and check for user reviews and ratings to ensure the software’s legitimacy. Additionally, keeping your antivirus software up-to-date can help detect and block any computer virus threats from unverified downloads, protecting your system from potential harm.
Safe Download Practices
Practicing safe download habits is essential to prevent a computer virus from infecting your system. Always download software from reputable and official websites, avoiding third-party sites that might offer compromised versions. Trusted sources ensure that the files you download are free from malicious code designed to spread a computer virus.
Using robust antivirus software is another crucial step in safe download practices. Antivirus programs can scan files before they are downloaded and block any that contain a computer virus. Keeping your antivirus software updated ensures it can recognize and protect against the latest threats, providing an additional layer of security against malicious downloads.
Finally, be cautious with email attachments and links, even if they appear to come from known contacts. Cybercriminals often use phishing tactics to spread a computer virus through seemingly legitimate downloads. Verify the sender’s identity and scan any attachments with antivirus software before opening them to avoid malicious downloads and keep your system safe.
3. Infected Removable Media

Infected removable media, such as USB drives and external hard drives, can be a major source of computer virus infections. When these devices are connected to your computer, they can automatically transfer malicious software if proper precautions aren’t taken. Always scan removable media with a reliable antivirus program before accessing any files to prevent virus infiltration.
To mitigate risks from infected removable media, disable the autoplay feature on your computer. This prevents any automatic execution of malicious software when the device is connected. Be cautious when using shared or borrowed removable media, as they might carry hidden threats. Educate yourself on the signs of a potential computer virus, such as unexpected file behavior or sudden system slowdowns.
Adopting best practices for using removable media can significantly reduce the risk of computer virus infections. Regularly update your antivirus software to ensure it can detect the latest threats. Avoid using removable media from untrusted sources, and always back up important data to secure locations. By following these guidelines, you can keep your computer safe from viruses spread through infected removable media.
How Viruses Use USB Drives and CDs
Computer viruses often exploit USB drives and CDs as vectors to spread and infect systems. These removable media devices can unknowingly carry malicious software that activates when connected to a computer. To protect your system, always scan USB drives and CDs with a reliable antivirus program before accessing their contents.
Auto-run features in operating systems can make USB drives and CDs particularly vulnerable to computer virus infections. When a device is connected, the auto-run feature can execute harmful files automatically. Disabling auto-run settings and manually scanning media before opening files can prevent these stealthy infections and keep your system secure.
To prevent computer virus infections from USB drives and CDs, adopt safe usage practices. Avoid using removable media from unknown or untrusted sources, and ensure that your antivirus software is up to date to detect the latest threats. Regularly back up important data and stay informed about new virus threats to maintain a robust defense against infections spread through these common devices.
Precautions to Take
Taking essential precautions can significantly reduce the risk of computer virus infections. Always use reputable antivirus software and keep it updated to protect against the latest threats. Regularly scan your computer for viruses and malware to catch any potential infections early. By staying vigilant and proactive, you can maintain a secure system.
Practicing safe browsing habits is crucial in preventing computer virus infections. Avoid clicking on suspicious links or downloading files from untrusted websites. Ensure that your web browser’s security settings are configured to block malicious downloads and phishing attempts. These precautions help safeguard your computer against viruses that lurk online.
Keeping your software and operating system up to date is a vital precaution to protect against computer viruses. Updates often include patches for security vulnerabilities that viruses exploit. Enable automatic updates to ensure your system is always protected with the latest security enhancements. By doing so, you create a robust defense against potential computer virus infections.
4. Network Connections

Securing your network connections is vital to preventing computer virus infections. Ensure your Wi-Fi network is protected with a strong password and encryption, such as WPA3. Regularly update your router’s firmware to patch vulnerabilities. By securing your network, you create a robust barrier against viruses attempting to infiltrate through unsecured connections.
Monitoring your network for suspicious activity can help prevent computer virus infections. Use network security tools to detect unusual traffic patterns or unauthorized devices. Implementing a firewall adds an extra layer of protection, blocking potential threats before they can reach your computer. Staying vigilant about network activity is key to maintaining a virus-free environment.
Adopting best practices for network usage can significantly reduce the risk of computer virus infections. Avoid connecting to public Wi-Fi networks without a VPN, as they are often targets for hackers. Ensure all connected devices have updated antivirus software and firewalls enabled. By following these guidelines, you can safeguard your computer from viruses spread through network connections.
Spread Through Shared Networks
Computer viruses can easily spread through shared networks, making it crucial to understand how these infections occur. When devices are connected to the same network, viruses can transfer from one compromised system to others. Ensuring all devices on a shared network have updated antivirus software can help prevent the spread of infections and protect your data.
To prevent computer virus infections on shared networks, implement strong network security measures. Use firewalls to block unauthorized access and regularly update all software and devices connected to the network. Educate users about safe online practices, such as avoiding suspicious links and downloads, to reduce the risk of virus transmission.
Adopting best practices for network sharing can minimize the risk of computer virus infections. Avoid sharing sensitive files over unsecured networks and use encryption for data transfers. Regularly monitor network activity for any signs of unauthorized access or unusual behavior. By following these guidelines, you can create a safer network environment and prevent the spread of computer viruses.
Protecting Network Security
Protecting your network security is crucial to preventing computer virus infections. Start by using strong, unique passwords for all network devices and enabling WPA3 encryption for your Wi-Fi. Regularly update your router’s firmware and use a robust antivirus program to safeguard your network from potential threats. These steps ensure a secure environment, reducing the risk of virus infiltration.
Firewalls are a critical component of network security, acting as a barrier between your computer and potential threats. They monitor incoming and outgoing traffic, blocking malicious activities and preventing computer virus infections. Make sure to configure your firewall settings properly and keep them updated to provide continuous protection for your network.
Educating all users about network security practices is essential in preventing computer virus infections. Encourage safe browsing habits, such as avoiding suspicious links and downloads. Regularly update software and use secure connections, especially when accessing sensitive information. By promoting awareness and good habits, you can create a strong defense against computer viruses across your network.
5. Social Engineering
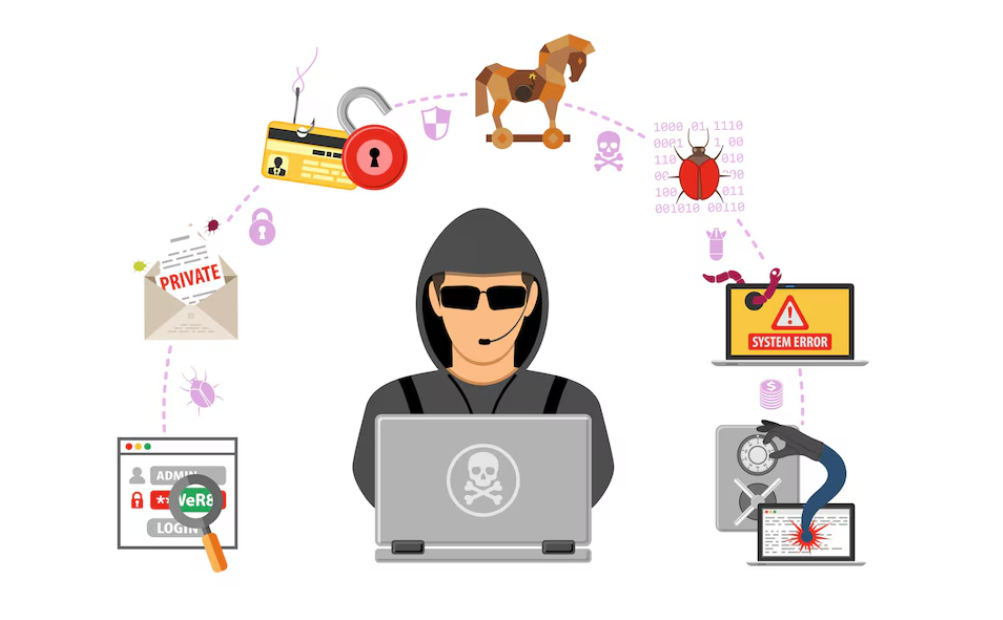
Social engineering is a manipulative technique used by cybercriminals to spread computer viruses. These attackers exploit human psychology, tricking individuals into revealing sensitive information or downloading malicious files. By recognizing common social engineering tactics, such as phishing emails and fraudulent phone calls, you can protect yourself from falling victim to these deceptive schemes.
Awareness is key to preventing computer virus infections through social engineering. Always verify the identity of individuals requesting sensitive information and be cautious of unsolicited communications. Never click on suspicious links or download attachments from unknown sources. By staying informed and vigilant, you can reduce the risk of being manipulated by social engineering attacks.
Implementing best practices can help safeguard against social engineering and the computer virus threats it poses. Educate yourself and your team about the dangers of social engineering and encourage the use of strong, unique passwords. Regularly update antivirus software and perform security awareness training. These measures create a robust defense, protecting your system from social engineering-based computer virus infections.
Manipulative Tactics Used by Hackers
Hackers often use manipulative tactics to spread computer viruses, exploiting human behavior to gain access to sensitive information. Phishing emails that appear legitimate can trick users into clicking malicious links or downloading infected files. By understanding these tactics, such as fake software updates and counterfeit websites, you can better protect your system from computer viruses.
Hackers deploy various manipulative strategies to infect computers with viruses. Social engineering attacks, such as posing as trusted entities, can deceive individuals into revealing confidential data. Pop-up ads that claim your system is infected are another common tactic. Being aware of these strategies helps you avoid falling victim to such schemes and keeps your computer virus-free.
Implementing protective measures is crucial to defend against hacker manipulation and computer virus infections. Use robust antivirus software to detect and block malicious activities. Avoid clicking on suspicious links and verify the authenticity of any unexpected messages or downloads. Educating yourself about these manipulative tactics empowers you to maintain a secure and virus-free computing environment.
How to Avoid Falling Victim
To avoid falling victim to computer virus attacks, always exercise caution when dealing with emails and downloads. Only open attachments from trusted sources and verify the legitimacy of links before clicking on them. Using a reliable antivirus program that scans and protects your system in real-time can significantly reduce the risk of infection.
Implementing strong security practices is crucial in preventing computer virus infections. Regularly update your operating system and software to patch vulnerabilities that viruses might exploit. Enable firewalls to block unauthorized access and ensure your antivirus software is always up to date. These measures help create a robust defense against potential threats.





1 Comment
Thanks 👍